Building the Admin Area (Tier0) is a challenge on its own. This area is not only the OU subtree, but many other containers, which will have the “accessing” groups stored here.
There are several steps to build this tier:
- Organizational Units
- Move objects
- Default Administrators Accounts
- Creating Groups
- Fine Grained Password Policy
- Group Nesting
- Modify AdminSdHolder
- Default Container Redirection
- Initial setup of Servers Area (Tier1)
- Initial setup of Sites Area (Tier2)
- Start with Delegations
Organizational Units needed to build Admin Area (Tier0)
We will start with the “Admin” Organizational Unit. When creating an OU, this one does have inherit permissions from the parent, which might become a issue when dealing with high privileged accounts. For example, if there is a rouge delegation at the domain level, which can reset AD User password, this one will be applied to this new Admin OU, which is a security risk.
We start by creating our OU:
New-DelegateAdOU -?
NAME
New-DelegateAdOU
SYNOPSIS
Create New custom delegated AD OU
SYNTAX
New-DelegateAdOU [-ouName] <String> [-ouPath] <String> [-ouDescription] <String>] [-ouCity] <String>] [-ouCountry] <String>] [-ouStreetAddress]
<String>] [-ouState] <String>] [-ouZIPCode] <String>] [-strOuDisplayName] <String>] [-RemoveAuthenticatedUsers]] [-CleanACL] [-WhatIf] [-Confirm]
[<CommonParameters>]
DESCRIPTION
Create New custom delegated AD OU, and remove
some groups as Account Operators and Print Operators
This will create the OU, with all pre-defined ACL’s (including Orphan SIDs) and inheritance. And as we already mention, is not what we want. So now that we have this OU, we have to block inheritance, copy ACLs and “Clan it up”; this is done by removing inheritance, and copying the inherited ACLs; then we do remove all of those ACEs that we do not need, as is the case of “Pre-Windows 2000”, “Account Operators” and “Print Operators”. We also be removing any orphan SID (this SID on the ACE which cannot be resolved to a name, most likely because the object was deleted) and any other delegation that might interfere with the setup we are doing here. We will end up with something similar to this:
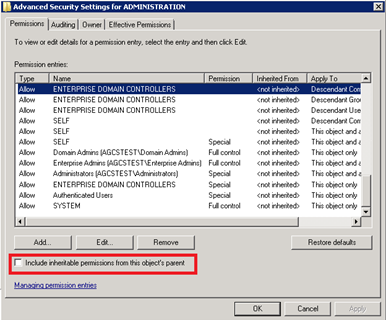
In order to automate the build of Admin Area (Tier0), EguibarIT PowerShell Module provides some CMDlets that can help:
New-DelegateAdOU
New-DelegateAdOU -?
NAME
New-DelegateAdOU
SYNOPSIS
Create New custom delegated AD OU
SYNTAX
New-DelegateAdOU [-ouName] <String> [-ouPath] <String> [-ouDescription] <String>] [-ouCity] <String>] [-ouCountry] <String>] [-ouStreetAddress]
<String>] [-ouState] <String>] [-ouZIPCode] <String>] [-strOuDisplayName] <String>] [-RemoveAuthenticatedUsers]] [-CleanACL] [-WhatIf] [-Confirm]
[<CommonParameters>]
DESCRIPTION
Create New custom delegated AD OU, and remove
some groups as Account Operators and Print Operators
This is a wrapper functions that 1) Checks for OU existence, and create it if doe not exist 2) Calls “Start-AdCleanOU” to remove unwanted ACEs 3) Call “Remove-SpecificACLandEnableInheritance” to manage inheritance and specific ACEs
Start-AdCleanOU
Start-AdCleanOU -?
NAME
Start-AdCleanOU
SYNOPSIS
Clean default OU permissions.
SYNTAX
Start-AdCleanOU [-LDAPpath] <String> [[-RemoveAuthenticatedUsers]] [[-RemoveUnknownSIDs]] [<CommonParameters>]
DESCRIPTION
The function will remove some of the default premission on
the provided OU. It will remove the "Account Operators" and
"Print Operators" built-in groups
This is another wrapper function that provides functionality to clean any other OU. It relies on EguibarIT.Delegation PowerShell Module CMDlets.
$parameters = @{
Group = ’Account Operators’
LDAPPath = ’LDAPPath’
RemoveRule = $true
}
# Remove the Account Operators group from ACL to Create/Delete Users
Set-AdAclCreateDeleteUser @parameters
# Remove the Account Operators group from ACL to Create/Delete Computers
Set-AdAclCreateDeleteComputer @parameters
# Remove the Account Operators group from ACL to Create/Delete Groups
Set-AdAclCreateDeleteGroup @parameters
# Remove the Account Operators group from ACL to Create/Delete Contacts
Set-AdAclCreateDeleteContact @parameters
# Remove the Account Operators group from ACL to Create/Delete inetOrgPerson
Set-CreateDeleteInetOrgPerson @parameters
# Remove the Print Operators group from ACL to Create/Delete PrintQueues
Set-AdAclCreateDeletePrintQueue @parameters
# Remove Pre-Windows 2000 Compatible Access group from Admin-User
Remove-PreWin2000 -LDAPPath ’LDAPPath’
# Remove Pre-Windows 2000 Access group from OU
Remove-PreWin2000FromOU -LDAPPath ’LDAPPath’
# Remove ACCOUNT OPERATORS 2000 Access group from OU
Remove-AccountOperator -LDAPPath ’LDAPPath’
# Remove PRINT OPERATORS 2000 Access group from OU
Remove-PrintOperator -LDAPPath ’LDAPPath’
# Remove AUTHENTICATED USERS group from OU
Remove-AuthUser -LDAPPath ’LDAPPath’
# Remove Un-Resolvable SID from a given object
Remove-UnknownSID -LDAPPath ’LDAPPath’ -RemoveSID
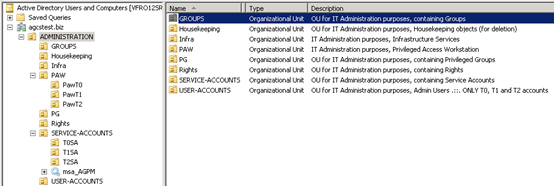
Creating the sub-OU structure
The following step is to create remaining OUs. By using these functions, we can optimize the creation of ANY OU that we might need, and as described before, building the Admin Area (Tier0). So the following sub-OU have to be created (but not limited to…):
| Sub-OU | Objects | Justification |
| Users | User Identities | Any user object which has administrative rights within the domain. The rights can be inherited, as the Administrator account, by group membership of privileged groups as Domain Admins or Account operators, or any other group used to delegate rights. This OU will have its own set of configurations for the users (GPO) and it will have a Fine Grained Password Policy. |
| Groups | Global/Universal Groups | This container will differentiate the organizational groups from the ones belonging to the Rights OU. These groups (as per definition) should only contain as members, users and other groups, and shall not be granted any right. Only Privileged, Semi-Privileged and Service Accounts can belong to these kinds of groups. This OU will have its own set of configurations for the computers (GPO). |
| Housekeeping | Users & Computers | Staled user objects and computer objects. An automated procedure will search for staled objects and move those to this container in order to delete when thresholds are met. |
| Infrastructure Services | Computers | Any server belonging to Tier0 and providing services exclusively to this area/tier. This could be the virtualization servers, patching servers, deployment servers, monitoring servers, etc. |
| Privileged Groups | Global/Universal Groups | Delegation model Privileged groups. |
| Privileged Access Workstations | Computers | Highly secured computers (known as PAW) used to administer the domain. RDP to manage Domain Controllers is not a desired practice, and doing so from a “standard” PC must be avoided by any means. Instead these designated management computers will fulfill this request. |
| PAW Tier0 | Computers | Privileged Access Workstation restricted exclusively for Administration Area / Tier0 |
| PAW Tier1 | Computers | Privileged Access Workstation restricted exclusively for Servers Area / Tier1 |
| PAW Tier2 | Computers | Privileged Access Workstation restricted exclusively for Sites Area / Tier2 |
| Rights | Domain Local Groups | Any ACL granting access within the domain has to be assigned to these groups. This container will only have groups which are delegated rights. Although this container could be merged with the Groups one, is a good idea to have clearly identified the standard groups (As the ones in the groups container, which its SACLs are not modified nor assigned to any other system object) from the groups which DO have additional access rights. |
| Service Accounts | User/Service Identities | By design, a service account should be guarded and kept extremely secured. Whenever possible, a ServiceAccount object should be created instead. If a ServiceAccount object cannot be created, additional security measures should be implemented. This OU will have its own set of configurations for the users (GPO) and it will have a Fine Grained Password Policy. |
| Service-Accounts Tier 0 | User/Service Identities | Service Accounts and/or Managed Service Accounts used exclusively for Administration Area / Tier0 |
| Service-Accounts Tier 1 | User/Service Identities | Service Accounts and/or Managed Service Accounts used exclusively for Servers Area / Tier1 |
| Service-Accounts Tier 2 | User/Service Identities | Service Accounts and/or Managed Service Accounts used exclusively for Sites Area / Tier2 |
$Splat = @{
ouPath = $ItAdminOuDn
CleanACL =$True
}
New-DelegateAdOU -ouName $ItAdminAccountsOu -ouDescription $confXML.n.Admin.OUs.ItAdminAccountsOU.description @Splat
New-DelegateAdOU -ouName $ItAdminGroupsOU -ouDescription $confXML.n.Admin.OUs.ItAdminGroupsOU.description @Splat
New-DelegateAdOU -ouName $ItPrivGroupsOU -ouDescription $confXML.n.Admin.OUs.ItPrivGroupsOU.description @Splat
New-DelegateAdOU -ouName $ItPawOu -ouDescription $confXML.n.Admin.OUs.ItPawOU.description @Splat
New-DelegateAdOU -ouName $ItRightsOu -ouDescription $confXML.n.Admin.OUs.ItRightsOU.description @Splat
New-DelegateAdOU -ouName $ItServiceAccountsOu -ouDescription $confXML.n.Admin.OUs.ItServiceAccountsOU.description @Splat
New-DelegateAdOU -ouName $ItHousekeepingOu -ouDescription $confXML.n.Admin.OUs.ItHousekeepingOU.description @Splat
New-DelegateAdOU -ouName $ItInfraOu -ouDescription $confXML.n.Admin.OUs.ItInfraOU.description @Splat
New-DelegateAdOU -ouName $ItAdminSrvGroups -ouDescription $confXML.n.Admin.OUs.ItAdminSrvGroups.description @Splat
# Ensure inheritance is enabled for child Admin OUs
$Splat = @{
RemoveInheritance = $false
RemovePermissions = $True
}
Set-AdInheritance -LDAPPath $ItAdminAccountsOuDn @Splat
Set-AdInheritance -LDAPPath $ItAdminGroupsOUDn @Splat
Set-AdInheritance -LDAPPath $ItPrivGroupsOUDn @Splat
Set-AdInheritance -LDAPPath $ItPawOuDn @Splat
Set-AdInheritance -LDAPPath $ItRightsOuDn @Splat
Set-AdInheritance -LDAPPath $ItServiceAccountsOuDn @Splat
Set-AdInheritance -LDAPPath $ItHousekeepingOuDn @Splat
Set-AdInheritance -LDAPPath $ItInfraOuDn @Splat
# PAW Sub-OUs
$Splat = @{
ouPath = $ItPawOuDn
CleanACL =$True
}
New-DelegateAdOU -ouName $ItPawT0Ou -ouDescription $confXML.n.Admin.OUs.ItPawT0OU.description @Splat
New-DelegateAdOU -ouName $ItPawT1Ou -ouDescription $confXML.n.Admin.OUs.ItPawT1OU.description @Splat
New-DelegateAdOU -ouName $ItPawT2Ou -ouDescription $confXML.n.Admin.OUs.ItPawT2OU.description @Splat
New-DelegateAdOU -ouName $ItPawStagingOu -ouDescription $confXML.n.Admin.OUs.ItPawStagingOU.description @Splat
# Ensure inheritance is enabled for child Admin OUs
$Splat = @{
RemoveInheritance = $false
RemovePermissions = $True
}
Set-AdInheritance -LDAPPath $ItPawT0OuDn @Splat
Set-AdInheritance -LDAPPath $ItPawT1OuDn @Splat
Set-AdInheritance -LDAPPath $ItPawT2OuDn @Splat
Set-AdInheritance -LDAPPath $ItPawStagingOuDn @Splat
# Service Accounts Sub-OUs
$Splat = @{
ouPath = $ItServiceAccountsOuDn
CleanACL =$True
}
New-DelegateAdOU -ouName $ItSAT0OU -ouDescription $confXML.n.Admin.OUs.ItSAT0OU.description @Splat
New-DelegateAdOU -ouName $ItSAT1OU -ouDescription $confXML.n.Admin.OUs.ItSAT1OU.description @Splat
New-DelegateAdOU -ouName $ItSAT2OU -ouDescription $confXML.n.Admin.OUs.ItSAT2OU.description @Splat
# Ensure inheritance is enabled for child Admin OUs
$Splat = @{
RemoveInheritance = $false
RemovePermissions = $True
}
Set-AdInheritance -LDAPPath $ItSAT0OuDn @Splat
Set-AdInheritance -LDAPPath $ItSAT1OuDn @Splat
Set-AdInheritance -LDAPPath $ItSAT2OuDn @Splat
# Infrastructure Servers Sub-OUs
$Splat = @{
ouPath = $ItInfraOuDn
CleanACL =$True
}
New-DelegateAdOU -ouName $ItInfraT0Ou -ouDescription $confXML.n.Admin.OUs.ItInfraT0.description @Splat
New-DelegateAdOU -ouName $ItInfraT1Ou -ouDescription $confXML.n.Admin.OUs.ItInfraT1.description @Splat
New-DelegateAdOU -ouName $ItInfraT2Ou -ouDescription $confXML.n.Admin.OUs.ItInfraT2.description @Splat
New-DelegateAdOU -ouName $ItInfraStagingOu -ouDescription $confXML.n.Admin.OUs.ItInfraStagingOU.description @Splat
# Ensure inheritance is enabled for child Admin OUs
$Splat = @{
RemoveInheritance = $false
RemovePermissions = $True
}
Set-AdInheritance -LDAPPath $ItInfraT0OuDn @Splat
Set-AdInheritance -LDAPPath $ItInfraT1OuDn @Splat
Set-AdInheritance -LDAPPath $ItInfraT2OuDn @Splat
Set-AdInheritance -LDAPPath $ItInfraStagingOuDn @Splat
We will end up having something similar to this:
Move objects to newly created Admin Area (Tier0)
After our “brand new” container was created, and that is secured, is time to move objects into it. There are many objects that cannot be moved (we are talking about many built-in domain local groups), but for those which can be moved.
Get-ADUser -Identity $AdminName | Move-ADObject -TargetPath $ItAdminAccountsOuDn
Get-ADUser -Identity $confXML.n.Admin.users.Guest.Name | Move-ADObject -TargetPath $ItAdminAccountsOuDn
Get-ADUser -Identity krbtgt | Move-ADObject -TargetPath $ItAdminAccountsOuDn
Get-ADGroup -Identity ’Domain Admins’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Identity ’Enterprise Admins’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Identity ’Schema Admins’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Identity ’Domain Controllers’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Identity ’Group Policy Creator Owners’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Identity ’Read-only Domain Controllers’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Identity ’Enterprise Read-only Domain Controllers’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Identity ’DnsUpdateProxy’ | Move-ADObject -TargetPath $ItAdminGroupsOuDn
Get-ADGroup -Identity ’Domain Users’ | Move-ADObject -TargetPath $ItAdminGroupsOuDn
Get-ADGroup -Identity ’Domain Computers’ | Move-ADObject -TargetPath $ItAdminGroupsOuDn
Get-ADGroup -Identity ’Domain Guests’ | Move-ADObject -TargetPath $ItAdminGroupsOuDn
Get-ADGroup -Identity ’Allowed RODC Password Replication Group’ | Move-ADObject -TargetPath $ItRightsOuDn
Get-ADGroup -Identity ’RAS and IAS Servers’ | Move-ADObject -TargetPath $ItRightsOuDn
Get-ADGroup -Identity ’DNSAdmins’ | Move-ADObject -TargetPath $ItRightsOuDn
Get-ADGroup -Identity ’Cert Publishers’ | Move-ADObject -TargetPath $ItRightsOuDn
Get-ADGroup -Identity ’Denied RODC Password Replication Group’ | Move-ADObject -TargetPath $ItRightsOuDn
# Following groups only exist on Win 2012
Get-ADGroup -Identity ’Protected Users’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Identity ’Cloneable Domain Controllers’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Identity ’Access-Denied Assistance Users’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Filter { SamAccountName -like "WinRMRemoteWMIUsers*" } | Move-ADObject -TargetPath $ItPrivGroupsOUDn
# Following groups only exist on Win 2019
Get-ADGroup -Identity ’Enterprise Key Admins’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
Get-ADGroup -Identity ’Key Admins’ | Move-ADObject -TargetPath $ItPrivGroupsOUDn
We need to have all important objects (Privileged and Semi-Privileged) under our control, thus the reason to have Admin Area.
Default Administrators Accounts
Although an Administrator default account can be tracked down by its well-known sid (SID ending with 500) is a good idea to rename it, and possibly disable it. I know there are many different discussions with regards of this, some of them in favor, and some of those against ir… but we are not going to enter this discussion here. Additionally, we will create a new Administrator Like account, which will have a normal SID instead. After initial setup, the well-known Administrator account should not be used; instead the Admin-Like account will be used. Both accounts should be heavily monitored, and of course, jealously guarded.
# Try to get the new Admin
$NewAdminExists = Get-AdUser -Filter { SamAccountName -eq $newAdminName }
# Check if the new Admin account already exist. If not, then create it.
If($NewAdminExists) {
#The user was found. Proceed to modify it accordingly.
$parameters = @{
Enabled = $true
UserPrincipalName = (‘{0}@{1}’ -f $newAdminName, $env:USERDNSDOMAIN)
SamAccountName = $newAdminName
DisplayName = $newAdminName
Description = $confXML.n.Admin.users.NEWAdmin.description
employeeId = ’0123456’
TrustedForDelegation = $false
AccountNotDelegated = $true
Company = $confXML.n.RegisteredOrg
Country = ’MX’
Department = $confXML.n.Admin.users.NEWAdmin.department
State = ’Puebla’
EmailAddress = (‘{0}@{1}’ -f $newAdminName, $env:USERDNSDOMAIN)
Replace = @{
’employeeType’ = $confXML.n.NC.AdminAccSufix0
’msNpAllowDialin’ = $false
’msDS-SupportedEncryptionTypes’ = ’24’
}
}
Set-AdUser -Identity $NewAdminExists
} Else {
# User was not Found! create new.
$parameters = @{
Path = $ItAdminAccountsOuDn
Name = $newAdminName
AccountPassword = (ConvertTo-SecureString -String $confXML.n.DefaultPassword -AsPlainText -Force)
ChangePasswordAtLogon = $false
Enabled = $true
UserPrincipalName = (‘{0}@{1}’ -f $newAdminName, $env:USERDNSDOMAIN)
SamAccountName = $newAdminName
DisplayName = $newAdminName
Description = $confXML.n.Admin.users.NEWAdmin.description
employeeId = ’0123456’
TrustedForDelegation = $false
AccountNotDelegated = $true
Company = $confXML.n.RegisteredOrg
Country = ’MX’
Department = $confXML.n.Admin.users.NEWAdmin.department
State = ’Puebla’
EmailAddress = (‘{0}@{1}’ -f $newAdminName, $env:USERDNSDOMAIN)
OtherAttributes = @{
’employeeType’ = $confXML.n.NC.AdminAccSufix0
’msNpAllowDialin’ = $false
’msDS-SupportedEncryptionTypes’ = ’24’
}
}
# Create the new Admin with special values
New-AdUser @parameters
$NewAdminExists = Get-AdUser -Identity $newAdminName
#http://blogs.msdn.com/b/openspecification/archive/2011/05/31/windows-configurations-for-kerberos-supported-encryption-type.aspx
# ’msDS-SupportedEncryptionTypes’= Kerberos DES Encryption = 2, Kerberos AES 128 = 8, Kerberos AES 256 = 16
} #end esle-if new user created
# Set the Protect against accidental deletions attribute
Get-AdUser -Identity $AdminName | Set-ADObject -ProtectedFromAccidentalDeletion $true
$NewAdminExists | Set-ADObject -ProtectedFromAccidentalDeletion $true
# Make it member of administrative groups
Add-AdGroupNesting -Identity ’Domain Admins’ -Members $NewAdminExists
Add-AdGroupNesting -Identity ’Enterprise Admins’ -Members $NewAdminExists
Add-AdGroupNesting -Identity ’Group Policy Creator Owners’ -Members $NewAdminExists
Add-AdGroupNesting -Identity ’Denied RODC Password Replication Group’ -Members $NewAdminExists
####
# Remove Everyone group from Admin-User & Administrator
Remove-Everyone -LDAPPath $NewAdminExists.DistinguishedName
Remove-Everyone -LDAPPath (‘CN={0},{1}’ -f $AdminName, $ItAdminAccountsOuDn)
####
# Remove AUTHENTICATED USERS group from Admin-User & Administrator
#Remove-AuthUser -LDAPPath $NewAdminExists.DistinguishedName
#Remove-AuthUser -LDAPPath (‘CN={0},{1}’ -f $AdminName, $ItAdminAccountsOuDn)
####
# Remove Pre-Windows 2000 Compatible Access group from Admin-User & Administrator
Remove-PreWin2000 -LDAPPath $NewAdminExists.DistinguishedName
Remove-PreWin2000 -LDAPPath (‘CN={0},{1}’ -f $AdminName, $ItAdminAccountsOuDn)
###
# Configure TheGood account
$params = @{
’employeeType’ = $confXML.n.NC.AdminAccSufix0
’msNpAllowDialin’ = $false
’msDS-SupportedEncryptionTypes’ = 24
}
Set-AdUser -Identity $AdminName -TrustedForDelegation $false -AccountNotDelegated $true -Add $params
Creating Groups
Now that we have the corresponding containers, we will start creating the corresponding groups (Global & Domain Local). Starting table contains the required Global Groups
| Security Principal | Description |
|---|---|
| SG_InfraAdmins | Full rights on all Active Directory infrastructure |
| SG_ADAdmins | Partial rights on all Active Directory infrastructure |
| SG_T0SA | Service Account for Tier 0 / Admin Area |
| SG_T1SA | Service Account for Tier 1 / Servers Area |
| SG_T2SA | Service Account for Tier 2 / Sites Area |
| SG_Tier0Admins | Administrators group for Tier 0 / Admin Area |
| SG_Tier1Admins | Administrators group for Tier 1 / Servers Area |
| SG_Tier2Admins | Administrators group for Tier 2 / Sites Area |
| SG_DfsAdmin | Full Rights to administer DFS |
| SG_GpoAdmin | Full Rights to administer GPO |
| SG_PkiAdmin | Full Rights to administer CA |
| SG_PkiTemplateAdmin | Full Rights to administer CA Templates |
| SG_AllGalAdmins | Delegated Limited general rights on all sites |
| SG_AllSiteAdmins | Limited general rights on all sites |
| SG_Operation | Limited rights on all Servers |
| SG_ServiceDesk | Password rights and AllGALAdmin rights on all sites |
| SG_ServerAdmin | Full administrative rights on servers |
| SG_GlobalGroupAdmin | Full Group administrative rights on all sites |
| SG_GlobalUserAdmin | Full user administrative rights on all sites |
| SG_GlobalPcAdmin | Full computer administrative rights on all sites |
This is the list of Domain Local required groups
| Security Principal | Description |
|---|---|
| SL_InfraRights | Delegated full rights to all AD infrastructure |
| SL_AdRights | Delegated partial rights to all AD infrastructure |
| SL_PUM | Rights for Privileged User management |
| SL_PGM | Right for Privileged Group management |
| SL_PISM | Right for Privileged Infrastructure management |
| SL_PAWM | Right for Privileged Access Workstation management |
| SL_DirReplRights | Right for Privileged Directory Replication Rights |
| SL_PkiRights | Right for Privileged Public Key Infrastructure management |
| SL_PkiTemplateRights | Right for Privileged Public Key Infrastructure Template management |
| SL_DfsRights | Right for Privileged DFS management |
| SL_GpoAdminRights | Right for Privileged GPO management |
| SL_UM | Rights for User Management |
| SL_GM | Rights for Group Management |
| SL_PSAM | Rights for Service Account Management |
| SL_InfrastructureServers | Rights for ALL Infrastructure Servers |
| SL_PAWs | Rights for ALL PAWs |
| SL_SvrAdmRight | Rights for server management |
| SL_SvrOpsRight | Rights for server operation management |
| SL_GlobalAppAccUserRight | Rights for Global Aplication Access Users |
| SL_GlobalGroupRight | Rights for Global Group Management |
Same as we did for OUs, there is a wrapper function for creating groups.
New-AdDelegatedGroup
Native New-AdGroup throws an error exception when the group already exists. This error is handled as a “correct” within this function due the fact that group might already exist and operation should continue, having the existing group modified. The function also can take care of removing unneeded groups, as Account Operators; or set the “Protect from accidental deletion” flag.
$splat = @{
Name = ’Poor Admins’
GroupCategory = ’Security’
GroupScope = ’DomainLocal’
DisplayName = ’Poor Admins’
Path = ’OU=Groups,OU=Admin,DC=EguibarIT,DC=local’
Description = ’New Admin Group’
ProtectFromAccidentalDeletion = $true
}
New-AdDelegatedGroup @Splat
This wrapper function uses some CMDLets from EguibarIT.Delegation PowerShell Module
Used Functions:
Name | Module
————————-|————————–
Get-CurrentErrorToDisplay | EguibarIT
Remove-AccountOperator | EguibarIT.Delegation
Remove-Everyone | EguibarIT.Delegation
Remove-AuthUser | EguibarIT.Delegation
Remove-PreWin2000 | EguibarIT.Delegation
Fine Grained Password Policy
The Default Domain Policy is not enough to secure Privileged & Semi-Privileged accounts. Instead create a Fine Grained Password policy and assign it to privileged admin accounts and groups. Same will be for Service Accounts
$PSOexists = $null
[String]$PsoName = $confXML.n.Admin.PSOs.ItAdminsPSO.Name
$PSOexists = Get-ADFineGrainedPasswordPolicy -Filter { name -eq $PsoName }
if(-not($PSOexists)) {
$parameters = @{
Name = $confXML.n.Admin.PSOs.ItAdminsPSO.Name
Precedence = $confXML.n.Admin.PSOs.ItAdminsPSO.Precedence
ComplexityEnabled = [System.Boolean]$confXML.n.Admin.PSOs.ItAdminsPSO.ComplexityEnabled
Description = $confXML.n.Admin.PSOs.ItAdminsPSO.Description
DisplayName = $confXML.n.Admin.PSOs.ItAdminsPSO.DisplayName
LockoutDuration = $confXML.n.Admin.PSOs.ItAdminsPSO.LockoutDuration
LockoutObservationWindow = $confXML.n.Admin.PSOs.ItAdminsPSO.LockoutObservationWindow
LockoutThreshold = $confXML.n.Admin.PSOs.ItAdminsPSO.LockoutThreshold
MaxPasswordAge = $confXML.n.Admin.PSOs.ItAdminsPSO.MaxPasswordAge
MinPasswordAge = $confXML.n.Admin.PSOs.ItAdminsPSO.MinPasswordAge
MinPasswordLength = $confXML.n.Admin.PSOs.ItAdminsPSO.MinPasswordLength
PasswordHistoryCount = $confXML.n.Admin.PSOs.ItAdminsPSO.PasswordHistoryCount
ReversibleEncryptionEnabled = [System.Boolean]$confXML.n.Admin.PSOs.ItAdminsPSO.ReversibleEncryptionEnabled
}
New-ADFineGrainedPasswordPolicy @parameters
$PSOexists = Get-ADFineGrainedPasswordPolicy -Filter { name -eq $PsoName }
} # End If PSO exists
# Apply the PSO to the corresponding accounts and groups
$parameters = @( $AdminName,
$newAdminName,
’Domain Admins’,
’Enterprise Admins’,
$SG_InfraAdmins.SamAccountName,
$SG_AdAdmins.SamAccountName,
$SG_GpoAdmins.SamAccountName,
$SG_Tier0Admins.SamAccountName,
$SG_Tier1Admins.SamAccountName,
$SG_Tier2Admins.SamAccountName,
$SG_Operations.SamAccountName,
$SG_ServerAdmins.SamAccountName,
$SG_AllSiteAdmins.SamAccountName,
$SG_AllGALAdmins.SamAccountName,
$SG_GlobalUserAdmins.SamAccountName,
$SG_GlobalPcAdmins.SamAccountName,
$SG_GlobalGroupAdmins.SamAccountName,
$SG_ServiceDesk.SamAccountName,
$SL_InfraRight.SamAccountName,
$SL_AdRight.SamAccountName,
$SL_UM.SamAccountName,
$SL_GM.SamAccountName,
$SL_PUM.SamAccountName,
$SL_PGM.SamAccountName,
$SL_GpoAdminRight.SamAccountName,
$SL_DnsAdminRight.SamAccountName,
$SL_DirReplRight.SamAccountName,
$SL_PromoteDcRight.SamAccountName,
$SL_TransferFSMOright.SamAccountName,
$SL_PISM.SamAccountName,
$SL_PAWM.SamAccountName,
$SL_PSAM.SamAccountName,
$SL_SvrAdmRight.SamAccountName,
$SL_SvrOpsRight.SamAccountName,
$SL_GlobalGroupRight.SamAccountName,
$SL_GlobalAppAccUserRight.SamAccountName
)
Add-ADFineGrainedPasswordPolicySubject -Identity $PSOexists -Subjects $parameters</code>”provider=”manual”lang=”php”/][pastacodemanual=”<code>$PSOexists = $null
[String]$PsoName = $confXML.n.Admin.PSOs.ServiceAccountsPSO.Name
$PSOexists = Get-ADFineGrainedPasswordPolicy -Filter { name -eq $PsoName }
if(-not($PSOexists)) {
$parameters = @{
Name = $confXML.n.Admin.PSOs.ServiceAccountsPSO.Name
Precedence = $confXML.n.Admin.PSOs.ServiceAccountsPSO.Precedence
ComplexityEnabled = [System.Boolean]$confXML.n.Admin.PSOs.ServiceAccountsPSO.ComplexityEnabled
Description = $confXML.n.Admin.PSOs.ServiceAccountsPSO.Description
DisplayName = $confXML.n.Admin.PSOs.ServiceAccountsPSO.DisplayName
LockoutDuration = $confXML.n.Admin.PSOs.ServiceAccountsPSO.LockoutDuration
LockoutObservationWindow = $confXML.n.Admin.PSOs.ServiceAccountsPSO.LockoutObservationWindow
LockoutThreshold = $confXML.n.Admin.PSOs.ServiceAccountsPSO.LockoutThreshold
MaxPasswordAge = $confXML.n.Admin.PSOs.ServiceAccountsPSO.MaxPasswordAge
MinPasswordAge = $confXML.n.Admin.PSOs.ServiceAccountsPSO.MinPasswordAge
MinPasswordLength = $confXML.n.Admin.PSOs.ServiceAccountsPSO.MinPasswordLength
PasswordHistoryCount = $confXML.n.Admin.PSOs.ServiceAccountsPSO.PasswordHistoryCount
ReversibleEncryptionEnabled = [System.Boolean]$confXML.n.Admin.PSOs.ServiceAccountsPSO.ReversibleEncryptionEnabled
}
New-ADFineGrainedPasswordPolicy @parameters
#$PSOexists = Get-ADFineGrainedPasswordPolicy -Filter { cn -eq $PsoName }
$PSOexists = Get-ADFineGrainedPasswordPolicy -Identity $PsoName
}
# Apply the PSO to all Tier Service Accounts
$parameters = @( $SG_Tier0ServiceAccount,
$SG_Tier1ServiceAccount,
$SG_Tier2ServiceAccount
)
Add-ADFineGrainedPasswordPolicySubject -Identity $PSOexists -Subjects $parameters
#endregion
Group Nesting
There is a lot to do when nesting groups. Instead, the following image will describe quite good the following PowerShell nesting code.
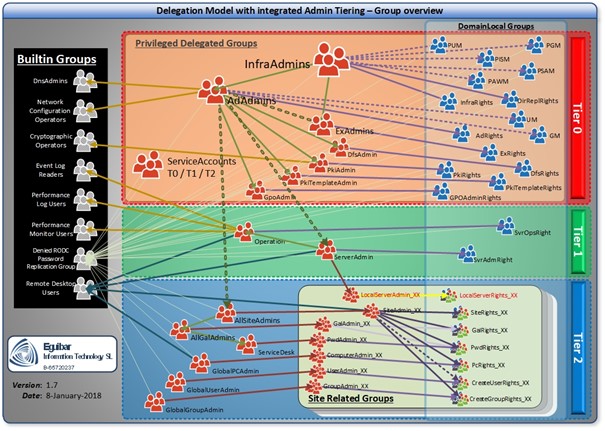
Same as other cases already mentioned, there is a wrapper function for group nesting. This is the same as Add-AdGroupMember but with error handling, managing duplicates an “already member” and logging.
#Nest Groups - Security for RODC
# Avoid having privileged or semi-privileged groups copy to RODC
Write-Verbose -Message ’Nesting groups…’
$parameters = @( $AdminName,
$newAdminName,
’Domain Admins’,
’Enterprise Admins’,
$SG_InfraAdmins,
$SG_AdAdmins,
$SG_GpoAdmins,
$SG_Tier0Admins,
$SG_Tier1Admins,
$SG_Tier2Admins,
$SG_Tier0ServiceAccount,
$SG_Tier1ServiceAccount,
$SG_Tier2ServiceAccount,
$SG_Operations,
$SG_ServerAdmins,
$SG_AllSiteAdmins,
$SG_AllGALAdmins,
$SG_GlobalUserAdmins,
$SG_GlobalPcAdmins,
$SG_GlobalGroupAdmins,
$SG_ServiceDesk,
$SL_InfraRight,
$SL_AdRight,
$SL_UM,
$SL_GM,
$SL_PUM,
$SL_PGM,
$SL_GpoAdminRight,
$SL_DnsAdminRight,
$SL_DirReplRight,
$SL_PromoteDcRight,
$SL_TransferFSMOright,
$SL_PISM,
$SL_PAWM,
$SL_PSAM,
$SL_SvrAdmRight,
$SL_SvrOpsRight,
$SL_GlobalGroupRight,
$SL_GlobalAppAccUserRight
)
Add-AdGroupNesting -Identity ’Denied RODC Password Replication Group’ -Members $parameters
#region Nest Groups - Delegate Rights through Builtin groups
# http://blogs.technet.com/b/lrobins/archive/2011/06/23/quot-admin-free-quot-active-directory-and-windows-part-1-understanding-privileged-groups-in-ad.aspx
# http://blogs.msmvps.com/acefekay/2012/01/06/using-group-nesting-strategy-ad-best-practices-for-group-strategy/
Add-AdGroupNesting -Identity ’Cryptographic Operators’ -Members $SG_AdAdmins
Add-AdGroupNesting -Identity ’Network Configuration Operators’ -Members $SG_AdAdmins
Add-AdGroupNesting -Identity DnsAdmins -Members $SG_AdAdmins
Add-AdGroupNesting -Identity ’Event Log Readers’ -Members $SG_AdAdmins, $SG_Operations
Add-AdGroupNesting -Identity ’Performance Log Users’ -Members $SG_AdAdmins, $SG_Operations
Add-AdGroupNesting -Identity ’Performance Monitor Users’ -Members $SG_AdAdmins, $SG_Operations
Add-AdGroupNesting -Identity ’Remote Desktop Users’ -Members $SG_AdAdmins
# https://technet.microsoft.com/en-us/library/dn466518(v=ws.11).aspx
$parameters = @($AdminName,
$NewAdminName,
$SG_InfraAdmins,
$SG_AdAdmins,
$SG_GpoAdmins,
$SG_Tier0Admins,
$SG_Tier1Admins,
$SG_Tier2Admins,
$SG_Operations,
$SG_ServerAdmins,
$SG_AllSiteAdmins,
$SG_AllGALAdmins,
$SG_GlobalUserAdmins,
$SG_GlobalPcAdmins,
$SG_GlobalGroupAdmins,
$SG_ServiceDesk
)
Add-AdGroupNesting -Identity ’Protected Users’ -Members $parameters
#endregion
#region Nest Groups - Extend Rights through delegation model groups
# http://blogs.msmvps.com/acefekay/2012/01/06/using-group-nesting-strategy-ad-best-practices-for-group-strategy/
# InfraAdmins as member of InfraRight
$parameters = @{
Identity = $SL_InfraRight
Members = $SG_InfraAdmins
}
Add-AdGroupNesting @parameters
# InfraAdmins as member of PUM
$parameters = @{
Identity = $SL_PUM
Members = $SG_InfraAdmins
}
Add-AdGroupNesting @parameters
# InfraAdmins as member of PGM
$parameters = @{
Identity = $SL_PGM
Members = $SG_InfraAdmins
}
Add-AdGroupNesting @parameters
# InfraAdmins as member of PISM
$parameters = @{
Identity = $SL_PISM
Members = $SG_InfraAdmins
}
Add-AdGroupNesting @parameters
# InfraAdmins as member of PAWM
$parameters = @{
Identity = $SL_PAWM
Members = $SG_InfraAdmins
}
Add-AdGroupNesting @parameters
# InfraAdmins as member of PSAM
$parameters = @{
Identity = $SL_PSAM
Members = $SG_InfraAdmins.SamAccountName
}
Add-AdGroupNesting @parameters
# InfraAdmins as member of Tier0Admins
$parameters = @{
Identity = $SG_Tier0Admins.SamAccountName
Members = $SG_InfraAdmins.SamAccountName
}
Add-AdGroupNesting @parameters
# InfraAdmins as member of DirReplRight
$parameters = @{
Identity = $SL_DirReplRight.SamAccountName
Members = $SG_InfraAdmins.SamAccountName
}
Add-AdGroupNesting @parameters
# InfraAdmins as member of AdAdmins
$parameters = @{
Identity = $SG_AdAdmins
Members = $SG_InfraAdmins
}
Add-AdGroupNesting @parameters
# AdAdmins as member of AdRight
$parameters = @{
Identity = $SL_AdRight
Members = $SG_AdAdmins
}
Add-AdGroupNesting @parameters
# AdAdmins as member of UM
$parameters = @{
Identity = $SL_UM
Members = $SG_AdAdmins
}
Add-AdGroupNesting @parameters
# AdAdmins as member of GM
$parameters = @{
Identity = $SL_GM
Members = $SG_AdAdmins
}
Add-AdGroupNesting @parameters
# AdAdmins as member of GpoAdmins
$parameters = @{
Identity = $SG_GpoAdmins
Members = $SG_AdAdmins
}
Add-AdGroupNesting @parameters
# AdAdmins as member of AllSiteAdmins
$parameters = @{
Identity = $SG_AllSiteAdmins
Members = $SG_AdAdmins
}
Add-AdGroupNesting @parameters
# AdAdmins as member of ServerAdmins
$parameters = @{
Identity = $SG_ServerAdmins
Members = $SG_AdAdmins
}
Add-AdGroupNesting @parameters
# GpoAdmins as member of GpoAdminRight
$parameters = @{
Identity = $SL_GpoAdminRight
Members = $SG_GpoAdmins
}
Add-AdGroupNesting @parameters
# AllSiteAdmins as member of AllGalAdmins
$parameters = @{
Identity = $SG_AllGALAdmins
Members = $SG_AllSiteAdmins
}
Add-AdGroupNesting @parameters
# AllGalAdmins as member of ServiceDesk
$parameters = @{
Identity = $SG_ServiceDesk
Members = $SG_AllGALAdmins
}
Add-AdGroupNesting @parameters
# ServerAdmins as member of SvrAdmRight
$parameters = @{
Identity = $SL_SvrAdmRight
Members = $SG_ServerAdmins
}
Add-AdGroupNesting @parameters
# Operations as member of SvrOpsRight
$parameters = @{
Identity = $SL_SvrOpsRight
Members = $SG_Operations
}
Add-AdGroupNesting @parameters
# ServerAdmins as member of Operations
$parameters = @{
Identity = $SG_Operations
Members = $SG_ServerAdmins
}
Add-AdGroupNesting @parameters
Modify AdminSdHolder
Delegation Model defines 2 “Privileged” groups which can modify privileged users and privileged groups respectively. In other word, a “Privileged User Manager (PUM)” group that its members cam change Domain Administrators (DA) without being members of the group. Same way, “Privileged Group Management (PGM) can change “Domain Admins”, “Enterprise Admins”, etc. without being a DA. EguibarIT.Delegation PowerShell Module provides 2 CMDLets for these purposes.
#Enabling Management Accounts to Modify the Membership of Protected Groups
# Enable PUM to manage Privileged Accounts (Reset PWD, enable/disable Administrator built-in account)
Set-AdAclMngPrivilegedAccounts -Group $SL_PUM.SamAccountName
# Enable PGM to manage Privileged Groups (Administrators, Domain Admins…)
Set-AdAclMngPrivilegedGroups -Group $SL_PGM.SamAccountName
Default Container Redirection
Default location for computers and users in AD is a simple folder; in other words, no specific GPO can be linked to these containers… something not good. This configuration section will create 2 OUs (Quarantine-Users & Quarantine-PCs), set the corresponding LOKDOWN GPO’s and have redirected the default location for each. Final result is that whenever a computer is domain joined without pre-staging the computer object (or without providing LDAP path destination while joining), it will end up in these new container; similar will happen to users.
#redirect Users & Computers containers
New-DelegateAdOU -ouName $ItQuarantineOu -ouPath $AdDn -ouDescription $confXML.n.Admin.OUs.ItNewComputersOU.description -RemoveAuthenticatedUsers
New-DelegateAdOU -ouName $confXML.n.Admin.OUs.ItNewUsersOU.Name -ouPath $AdDn -ouDescription $confXML.n.Admin.OUs.ItNewUsersOU.description -RemoveAuthenticatedUsers
# START Remove Delegation to BuiltIn groups BEFORE REDIRECTION
$parameters = @{
Group = ’Account Operators’
LDAPPath = ’CN=Computers,{0}’ -f $AdDn
RemoveRule = $True
}
### COMPUTERS
# Remove the Account Operators group from ACL to Create/Delete Users
Set-AdAclCreateDeleteUser @parameters
# Remove the Account Operators group from ACL to Create/Delete Computers
Set-AdAclCreateDeleteComputer @parameters
# Remove the Account Operators group from ACL to Create/Delete Groups
Set-AdAclCreateDeleteGroup @parameters
# Remove the Account Operators group from ACL to Create/Delete Contacts
Set-AdAclCreateDeleteContact @parameters
# Remove the Account Operators group from ACL to Create/Delete inetOrgPerson
Set-CreateDeleteInetOrgPerson @parameters
# Remove the Account Operators group from ACL to Create/Delete inetOrgPerson
Set-AdAclCreateDeletePrintQueue @parameters
$parameters = @{
Group = ’Account Operators’
LDAPPath = ’CN=Users,{0}’ -f $AdDn
RemoveRule = $True
}
### USERS
# Remove the Account Operators group from ACL to Create/Delete Users
Set-AdAclCreateDeleteUser @parameters
# Remove the Account Operators group from ACL to Create/Delete Computers
Set-AdAclCreateDeleteComputer @parameters
# Remove the Account Operators group from ACL to Create/Delete Groups
Set-AdAclCreateDeleteGroup @parameters
# Remove the Account Operators group from ACL to Create/Delete Contacts
Set-AdAclCreateDeleteContact @parameters
# Remove the Account Operators group from ACL to Create/Delete inetOrgPerson
Set-CreateDeleteInetOrgPerson @parameters
# Remove the Print Operators group from ACL to Create/Delete PrintQueues
Set-AdAclCreateDeletePrintQueue @parameters
###############################################################################
# Redirect Default USER & COMPUTERS Containers
redircmp.exe (‘OU={0},{1}’ -f $ItQuarantineOu, $AdDn)
redirusr.exe (‘OU={0},{1}’ -f $confXML.n.Admin.OUs.ItNewUsersOU.Name, $AdDn)
Initial setup of Servers Area (Tier1)
Create Servers (or other previously defined name) OU subtree. If any sub-OU already exists, just proceed to clean it up (The CMDlet Start-AdCleanOU from module EguibarIT can be used for this propose). As we are creating OUs, we will follow the same approach as we did on Organizational Units needed to build Admin Area (Tier0). This area/tier will only contain computer objects representing servers; any other related object should go into Sites Area (Tier2) or Admin Area (Tier0).
# SERVERS OU (area)
Write-Verbose -Message ’Creating Servers Area…’
###############################################################################
# Create Servers and Sub OUs
New-DelegateAdOU -ouName $ServersOu -ouPath $AdDn -ouDescription $confXML.n.Servers.OUs.ServersOU.Description
# Create Sub-OUs for Servers
New-DelegateAdOU -ouName $confXML.n.Servers.OUs.SqlOU.Name -ouPath $ServersOuDn -ouDescription $confXML.n.Servers.OUs.SqlOU.Description
New-DelegateAdOU -ouName $confXML.n.Servers.OUs.WebOU.Name -ouPath $ServersOuDn -ouDescription $confXML.n.Servers.OUs.WebOU.Description
New-DelegateAdOU -ouName $confXML.n.Servers.OUs.FileOU.Name -ouPath $ServersOuDn -ouDescription $confXML.n.Servers.OUs.FileOU.Description
New-DelegateAdOU -ouName $confXML.n.Servers.OUs.ApplicationOU.Name -ouPath $ServersOuDn -ouDescription $confXML.n.Servers.OUs.ApplicationOU.Description
New-DelegateAdOU -ouName $confXML.n.Servers.OUs.HypervOU.Name -ouPath $ServersOuDn -ouDescription $confXML.n.Servers.OUs.HypervOU.Description
New-DelegateAdOU -ouName $confXML.n.Servers.OUs.RemoteDesktopOU.Name -ouPath $ServersOuDn -ouDescription $confXML.n.Servers.OUs.RemoteDesktopOU.Description
Create the required management groups (SG_SvrAdmin, SL_SvrServerRiht, SG_Operations & SL_SvrOpsRight) as defined on the Delegation Model.
Initial setup of Sites Area (Tier2)
Create Sites (or other previously defined name) OU subtree. If any sub-OU already exists, just proceed to clean it up (The CMDlet Start-AdCleanOU from module EguibarIT can be used for this propose). As we are creating OUs, we will follow the same approach as we did on Organizational Units needed to build Admin Area (Tier0). This area/tier will contain all remaining objects, meaning anything apart from Tier0 used for administration of the environment, and servers; any other related object should go into Servers Area (Tier1) or Admin Area (Tier0).
Create Sites OUs (Area)
Write-Verbose -Message ’Creating Sites Area…’
New-DelegateAdOU -ouName $SitesOu -ouPath $AdDn -ouDescription $confXML.n.Sites.OUs.SitesOU.Description
As each and every site will be created individually, based on requirements, there is no need to create such administrative groups in advance.
Start with Delegations
Now that we have the right taxonomy & containers, and that we have the corresponding groups, we are ready to start delegating permissions and rights to these groups. We are halve the way on building our Admin Area (Tier0). Go to Delegating Admin Area (Tier0) page